Accelerated Ransomware Recovery
Recover faster and get back to business. Built-in orchestration and automation let you accelerate your recovery from ransomware.
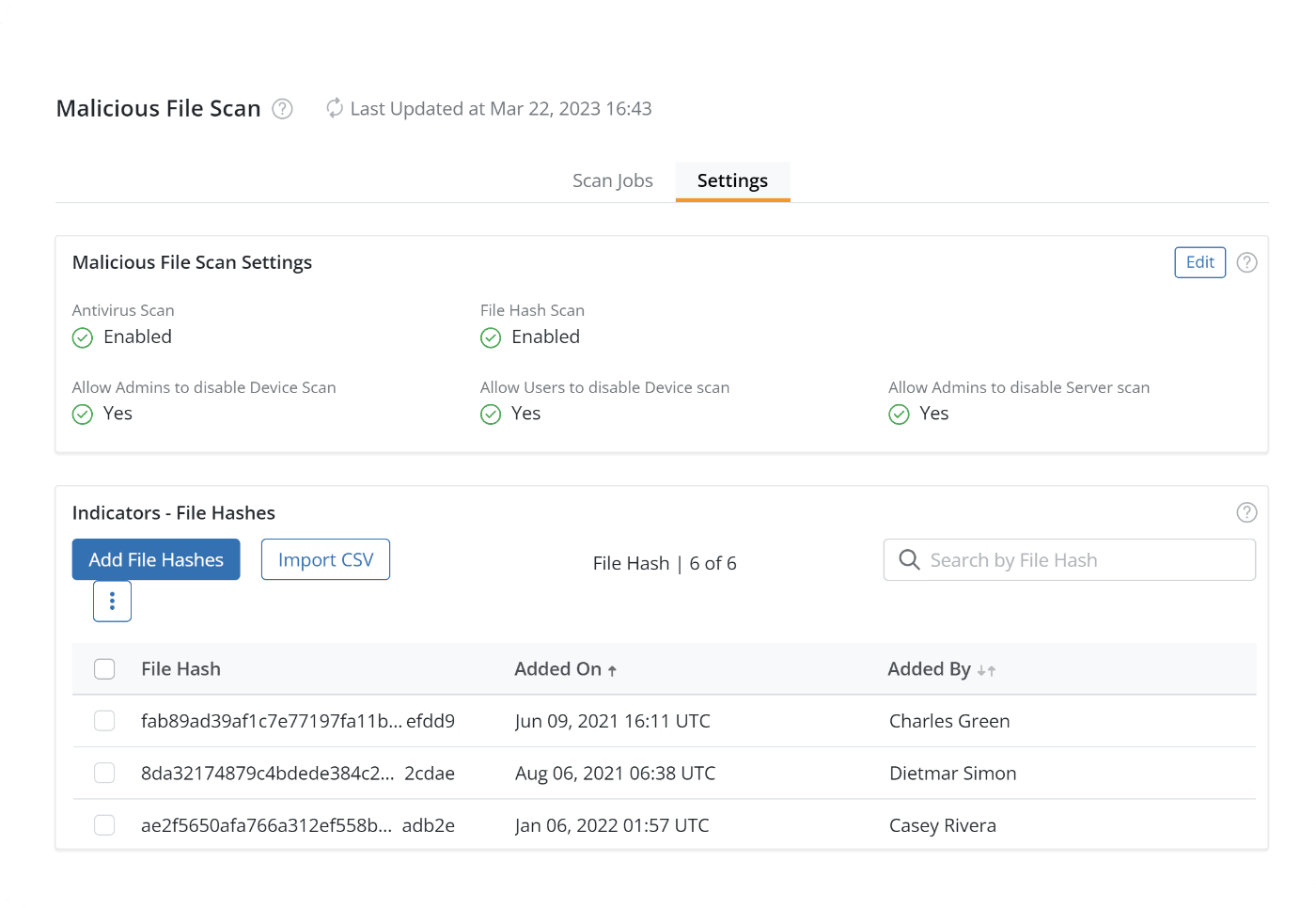
Ransomware is targeting backups
Ransomware attacks are increasingly targeting backups, but a fast and easy recovery will minimize downtime and get you back to business quickly.
![]()
Block attacks against your backups
Zero-trust security and 24x7 managed security operations enable operational security. Immutable, air-gapped backups ensure you have clean data to recover.
![]()
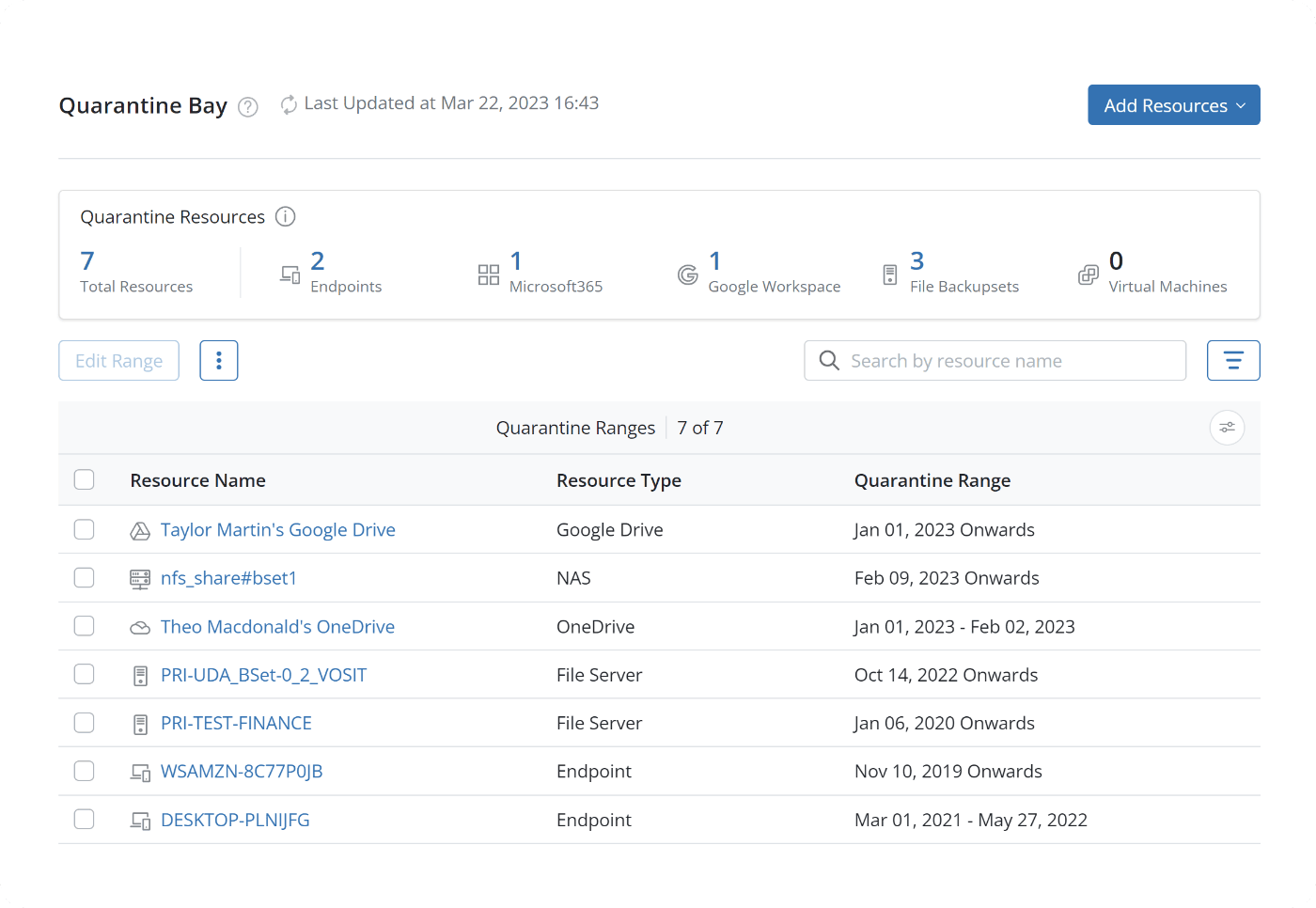
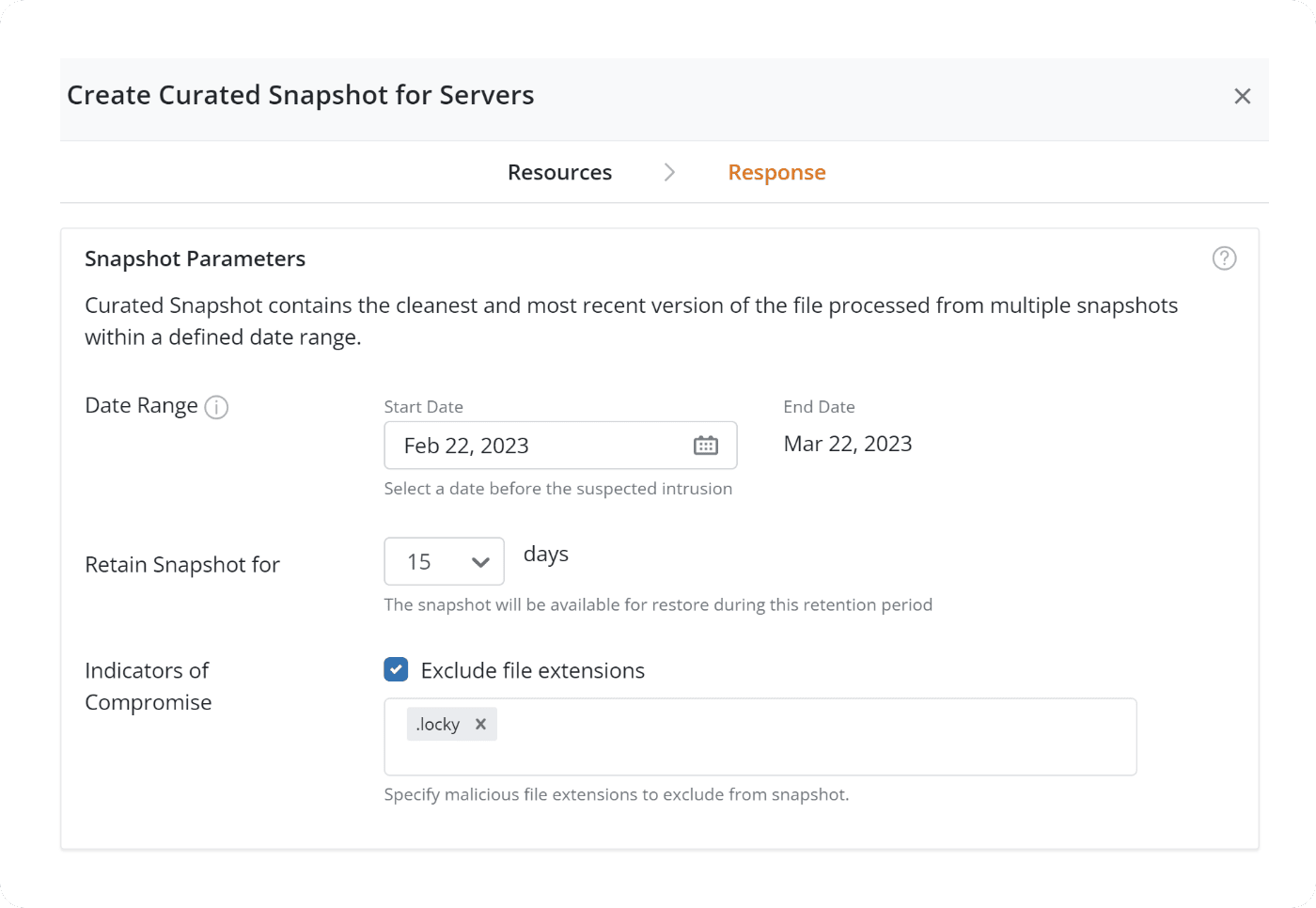
Accelerate ransomware recovery
Quickly identify unusual activity and prevent contamination spread within minutes of ransomware detection. Scan snapshots before recovery to eliminate reinfection.
![]()
Bridge the gap between backup and security systems
Help IT and security teams work together with built-in integrations with SIEM and SOAR tools to automate response and recovery.
Recover from ransomware fast
Druva’s advanced ransomware cloud data protection and defense-in-depth security are paired with
workflow orchestration and recovery automation tools to improve response time, prevent reinfection,
and reduce data loss. Plus, Druva’s SaaS solution delivers 24×7 fully-managed security operations.
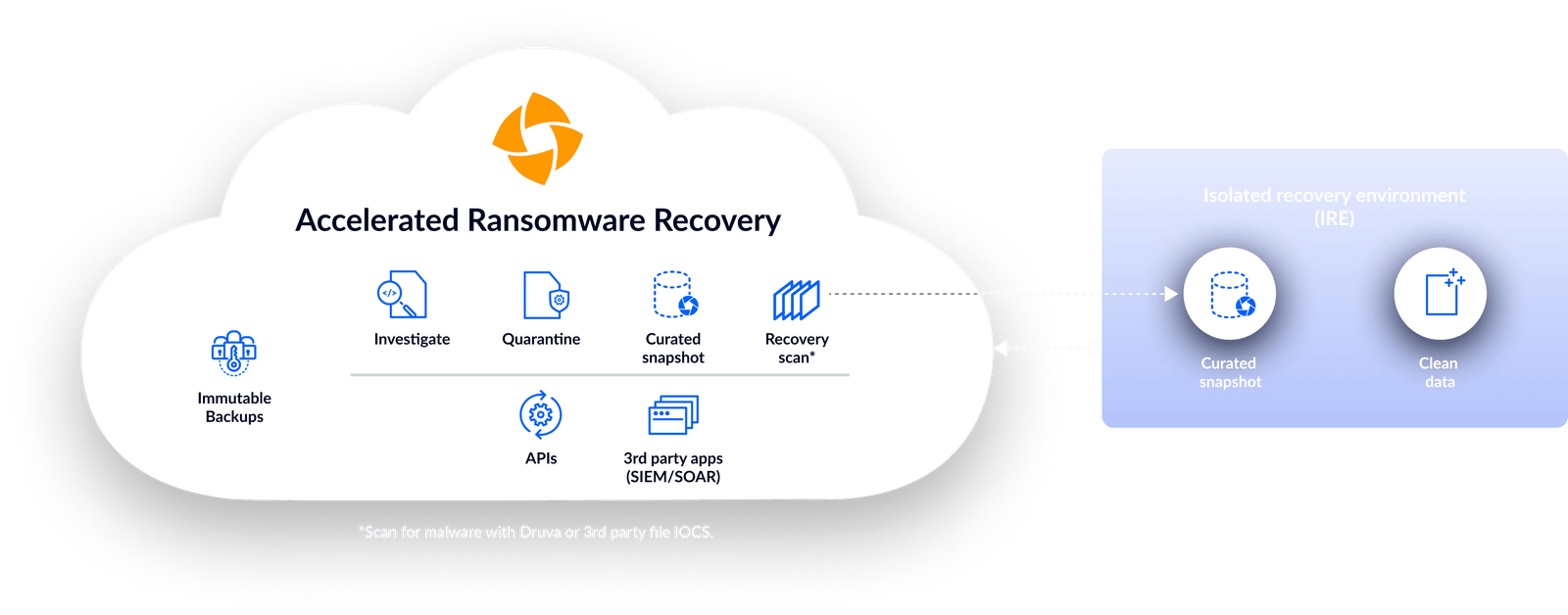
How it works
Stop threats to backups with a zero-trust architecture, immutable backups, and built-in security and observability across users, data, and activity.
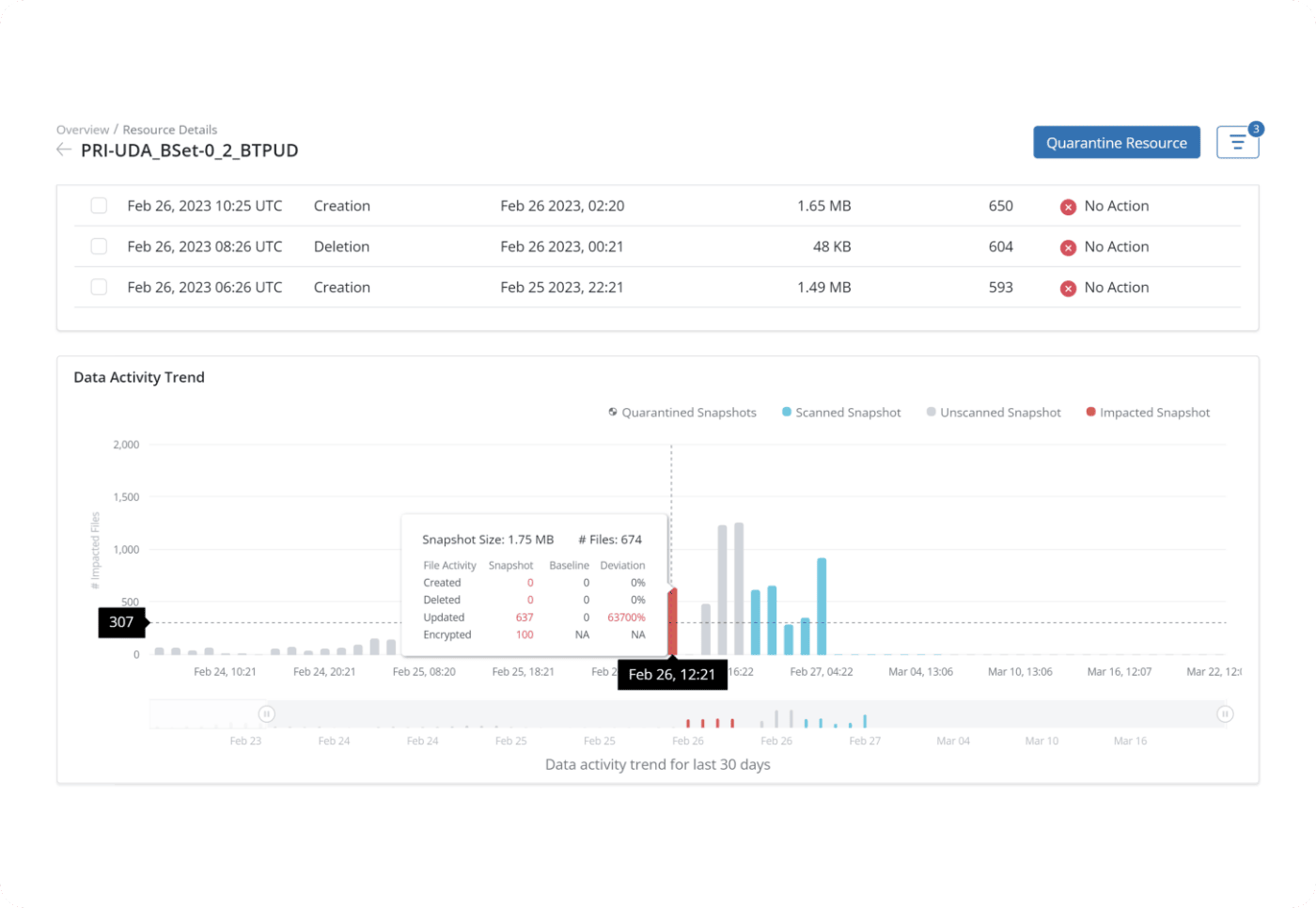
Visibility into unusual activity and point-in-time recoverability
Identify anomalies within backup data and choose the best snapshot for recovery with flexible recovery options.
The Druva Difference
Unlike on-premises or Windows-based solutions that may be vulnerable to ransomware, Druva’s cloud-native architecture provides a resilient operational environment that protects data and speeds up recovery.
Zero-trust security architecture
MFA and access controls prevent credential abuse, AES-256 encrypts data in flight and at rest.
Unusual data activity and user access insights
Entropy-based ML identifies backup anomalies; data and alerts are fed automatically to SIEM and SOAR tools.